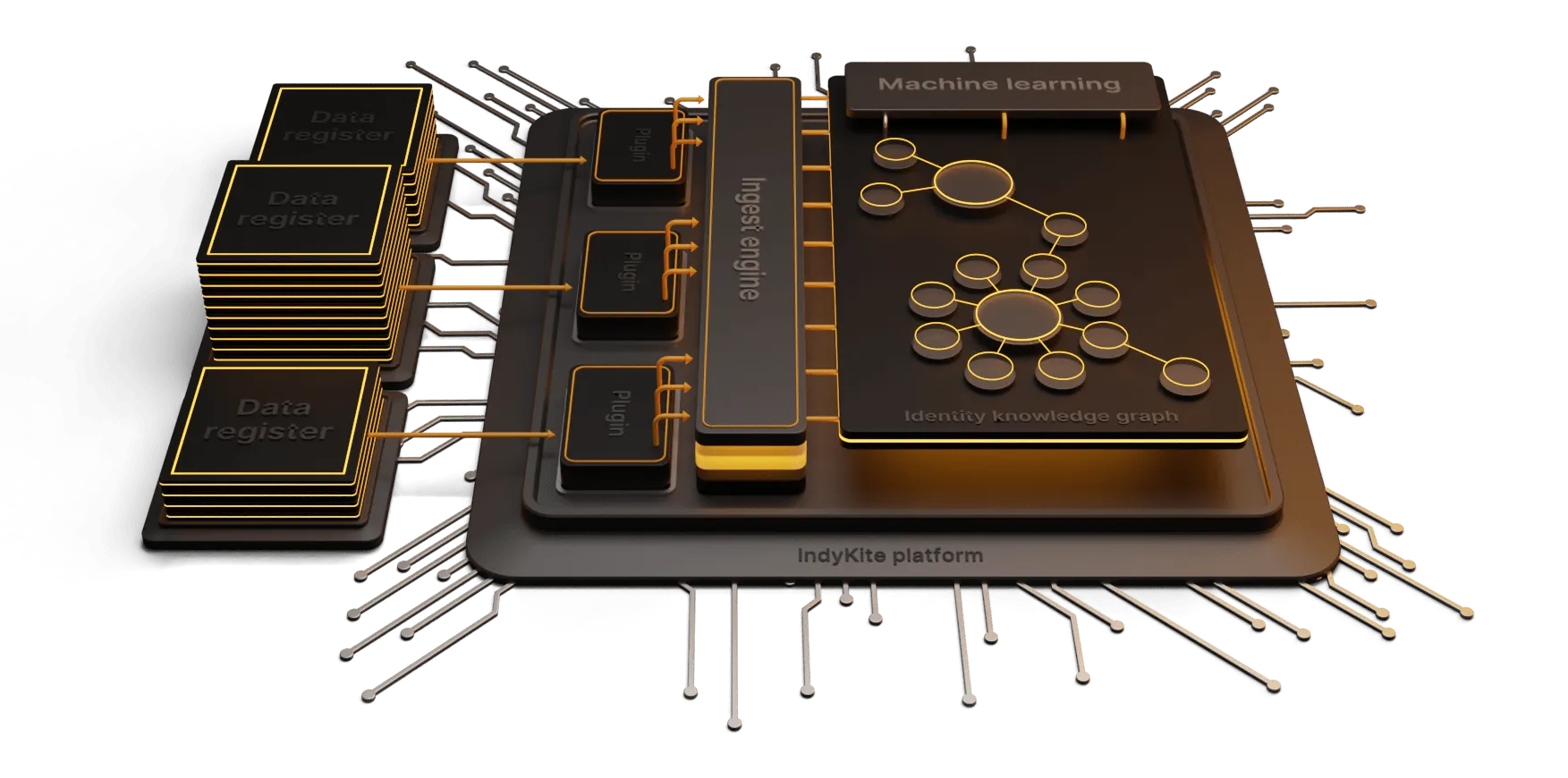
Technical debt is a pervasive problem and affects most organizations in some form or another. When looked at from a very broad view, it can be described as the negative effect of a short term perspective. There is a great Norwegian phrase that loosely translates to ‘pee your pants to keep warm’. Never a good strategy.
However, for most organizations, this isn’t quite capturing the challenge. Technical debt isn’t just the result of a lack of foresight, but limitations imposed by tooling, resources, skills and architecture, often that have built up over some time.
Identity and Access Management (IAM) systems are major culprits of legacy debt, traditionally designed to operate in silos, and once implemented are difficult to remove. Most large enterprises have several IAM systems in place, presenting a significant governance challenge.
Garnter recently released the paper, Reduce IAM Technical Debt, with key findings around reduced observability due to siloed IAM tooling, continued reliance on legacy solutions, human-identity management (neglecting non-human identities), and poor IAM hygiene hampering the effectiveness of IAM in an organization.
IAM technical debt arises when organizations accrue legacy systems, customized solutions, and fragmented IAM tools. Siloed architectures, interoperability limitations, and poor observability hinder organizations from effectively protecting against threats and ensuring compliance. Over time, technical debt accumulates, impeding efficient IAM controls and hindering the organization's ability to adapt to emerging security challenges.
A more modern approach to IAM can have a significant impact in reducing the burden of technical debt and limiting further accrual.
From fragmentation to unification
One of the biggest contributors to debt is fragmentation. With a unified approach to IAM and identity data, you can securely connect your IAM to your architecture in a way that protects sensitive information, while enabling interoperability.
By centralizing access decisions external to the applications and systems themselves, you can streamline and orchestrate authorization, ensuring consistent and accurate decisions, thereby reducing the challenge of governance. Further, an integrated and unified approach will bolster your security posture, creating a firmer perimeter and reducing the risk of error.
Benefits of unified identity data
Enhanced Observability
With a unified identity solution, organizations gain deep visibility into user access, permissions, and interactions across applications and systems. This improved observability fortifies security and aids in real-time detection and mitigation of threats.
Integrate modern IAM to enable broader infrastructure
IAM is a core enabler of business and when integrated and considered as part of an organization’s architecture, data can be aligned and leveraged to create broader value, enhance security, and uncover insights.
Simplified governance
A unified identity solution eliminates the complexities caused by managing multiple tools. Centralized administration and governance ensure consistent policies, reduce the risk of misconfigurations, and streamline IAM functions.
Flexible data model allows for change
Unlike traditional IAM, using a flexible data model allows you to evolve and scale without creating technical debt or locking into a single approach. This means you can implement gradually, use case by use case, leveraging what systems and data you already have, rather than requiring a software overhaul.
Support your existing use cases while enabling new solutions
A unified identity solution can handle more complexity than existing IAM tooling, allowing you to deliver new use cases that were previously impossible. This can be a powerful enabler for new products and services that require finer grained access controls or leveraging of contextual data for decisions.
Technical debt will continue to be a challenge for organizations, however it is possible to limit further accumulation and gradually reduce the technical debt you have. A unified identity solution can support this journey as a bridge towards a modern, open and interoperable stack, while still connecting and leveraging what you already have in place today.
In our next blog, we will explore how to implement simple steps to move toward this goal - while avoiding costly rip-and-replace projects.
If you want to learn more about how a unified identity approach can support your organization, book in for a free consultation with an Indykite team member or for a demo.