The unmet potential of the Customer Identity and Access Management Market in 2023
The CIAM market as it stands today has a pretty big problem. CIAM vendors often claim the importance of relationships in identity management, emphasizing its significance in delivering seamless experiences and personalized interactions. They market the hell out of these points, and rightly so, in CIAM, relationships are everything.
However, a lot of these vendors have a reliance on traditional databases or directories which hampers their ability to effectively manage and leverage relationships. These solutions - that make up the majority of today’s CIAM market - were not designed with relationships as a core consideration, resulting in limited flexibility, complex data modeling, inefficient performance, and most importantly, an inability to deliver genuine value to you and your customers.
To truly harness the power of relationships in CIAM, we need to look beyond the limitations of solutions that rely on traditional databases and directories (even the SaaS ones) and embrace innovative graph-based solutions, that are purpose-built to handle and leverage complex relationships in identity data, because, and I feel like it is important to repeat this, in CIAM, relationships are everything.
They are everything, but they are also everywhere. In this post, let's drive this home by looking at a few core aspects of CIAM - and their dependence on relationships - through the story of an end user, Alex.
Authentication
Beyond Usernames and Passwords
Authentication forms the foundation of secure access to your digital systems. While simple username/password authentication may suffice for basic scenarios, where the use of a LDAP directory may be sufficient, the complexity of CIAM depends on a more comprehensive approach.
Lets consider the multifaceted authentication decisioning scenarios Alex might encounter when interacting with your services. Questions arise: What authenticators are available to them? Are there constraints on their usage? Has Alex been granted access by a family member?
These requirements introduce relationships. Relationships between people, between accounts, between devices and things. Not only this, they introduce properties on the relationships themselves, such as usage constraints and context. A graph-based solution captures these relationships and ensures that authentication is not just a front door but a gateway to more personalized, convenient, and secure experiences.
Authorization
Embracing Complexity and Flexibility
Authorization is likely the area where organizations are most confronted with the limitations of traditional solutions when considering a modern CIAM strategy. Which isn’t great, given how important authorization has become for delivering great user experience and security. Simply put, proper authorization not only reduces friction and personalizes the user experience, but also safeguards consumer data. It is the make-or-break factor that renders your services usable, and the unique differentiator that makes your services enjoyable.
The challenge is actually doing authorization right when you are forced to conform to the constraints of traditional solutions, rather than adapting to the real-world, nuanced authorizations scenarios that make your products better and differentiate you from your competitors. This is likely only acceptable because all of your competitors are dealing with these constraints too!
With a graph-based solution, a retailer may offer Alex access to exclusive services due to their spending patterns or premium subscription, their bank can offer fine-grained control on their shared current account, and their phone provider can offer effortless device and plan management.
Again, all of these scenarios introduce relationships and properties on top of these relationships. By leveraging the relationships between these entities, organizations can unlock infinite possibilities and cater to unique authorization scenarios specific to their industries.
Privacy & Consent
Empowering Data Control and Compliance
Respecting user privacy and ensuring consent are vital pillars of CIAM. Managing consent and fine-grained control over data access can be very tricky with traditional solutions.
Alex’ journey intertwines with privacy and consent considerations. Who else has access to their premium subscription with the retailer? Are there specific constraints on their partners' access to the shared current account? Are there parental controls on the devices and plans Alex manages for their children? When was all of this consent given and does it expire?
With a graph-based solution like IndyKite, consent can be easily tracked as it is natively represented as an edge between the user and the relevant data. This allows you to navigate the intricate landscape of privacy and consent, instilling confidence, trust, and peace of mind with your customers.
Single Customer View
Unifying Identities and Relationships
A seamless and comprehensive view of your customer is a coveted goal of CIAM. However, achieving a single customer view is a complex task due to the dynamic nature of identities and relationships, and how many times removed entities may be. You also need flexibility in data modelling to accommodate diverse use cases, whether it's a bank managing accounts and transactions or a phone provider handling devices and plans.
We once again demonstrate the significance of relationships in CIAM and their impact on delivering a holistic view with Alex, their family, accounts, subscriptions, plans, and devices. Whatever the entities and their relationships might be, flexibility in the modelling, and being able to very quickly query relationships with entities that might be many edges away, is key for delivering a true single customer view.
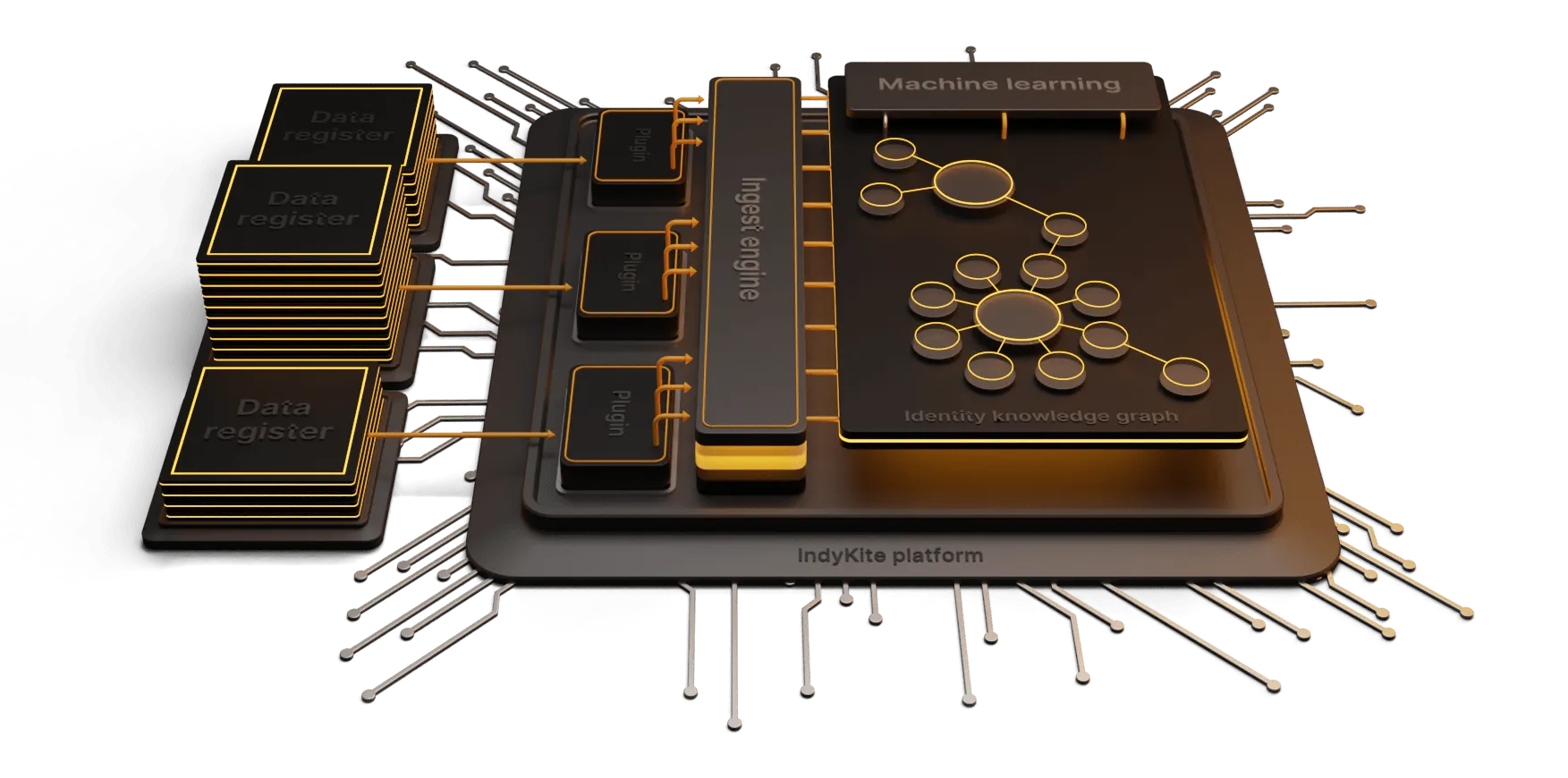
Additionally, the IndyKite Identity Knowledge Graph empowers organizations to integrate data from multiple sources, avoiding data silos and enabling a unified customer view that evolves with each interaction.
Customer Data Empowerment
Unleashing the Possibilities
Ultimately, the true power of a graph-based solution lies in empowering you and your customers. For you, it opens doors to innovative product lines, data-driven marketing strategies, sophisticated fraud analysis, and a reputation built on delivering secure and relevant experiences. For Alex, they benefit from streamlined and personalized experiences, with increased confidence in how their data is used and protected.
By leveraging the IndyKite Identity Knowledge Graph, organizations can unleash their creativity, leverage customer data in new ways, and offer innovative services that were previously unimaginable.
By embracing the power of relationships and adopting the IndyKite Identity Knowledge Graph as the foundation of CIAM, you can transform your approach, establish a competitive edge in today's digital landscape and deliver genuine value to you and your customers.
Afterall, in CIAM, relationships are everything.