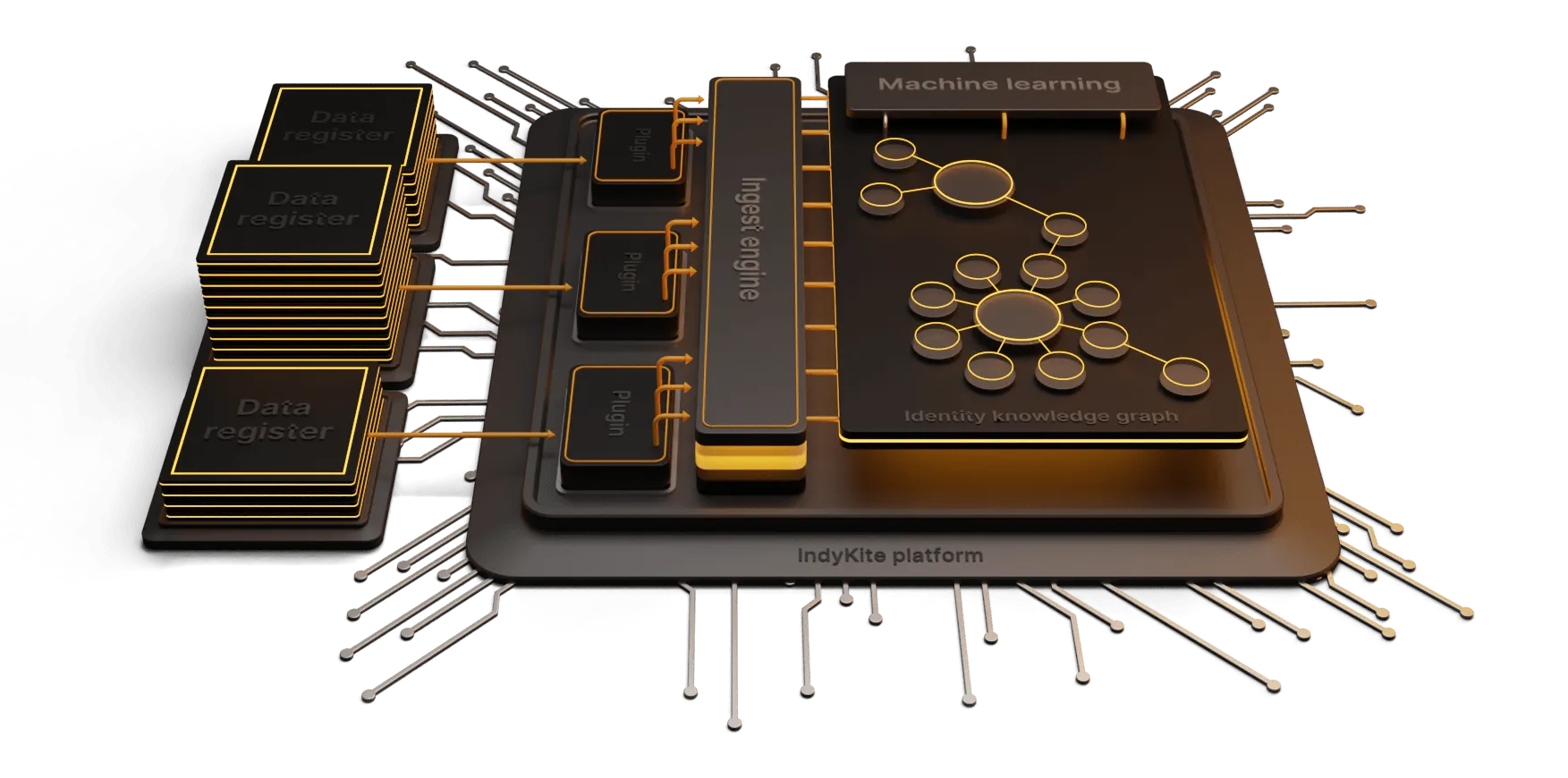
Much of the current authorization and access control landscape is centered around people. Who has access to what and based on what roles or attributes. At the same time, the world has evolved far beyond the era these technologies were originally designed for.
There are more bots, smart devices, machines, and other ‘things’ online than people. And this number is growing exponentially.
In many cases, these ‘things’ don’t just interact with people, but with each other. Any exchange of data requires a decision - an authorization decision - most of which have been coded into the connecting APIs (usually with coarse grained policies) and/or individual applications and operating systems (creating challenges for scalability and flexibility).
To solve this, many businesses are implementing dynamic, externalized authorization solutions, to ensure accurate, real time response and create consistent, flexible and scalable authorization across their various systems and applications.
These decisions shouldn’t be catch-all, coarse grained decisions, but granular and specific. The more granular, the more control the business has over how the data can be segmented and leveraged for various purposes.
Beyond devices and data interacting with one another lies another, highly lucrative use of data generated. Many businesses capture data and are looking for innovative ways to understand and use this data to drive efficiency gains across their supply chains. Beyond the use of this data for internal efficiency gains lies a marketplace waiting to be untapped. But where there are large quantities of data and bigger opportunities for monetization of this data, there are many challenges! Using the right authorization approach can make this an easy reality.
The digital transformation that we are seeing in most heavy manufacturing (among many other industries), stands to benefit dramatically from leveraging modern authorization for data streams.
For example, a vehicle manufacturer might want to monetize the maintenance, use and performance data collected by a vehicle’s internal systems as a subscription product to the vehicle’s future owners.
At scale, this can become a massive new revenue stream.
To make it a reality requires an access control solution granular enough to handle the complexity presented by the various data streams, as well as the complexity of the users who need various types of access to the data.
Traditional types of access control will struggle with this granularity and many implementers and product managers have resorted to building DIY authorization into the application itself (perhaps leveraging a flexible data model) to achieve the granularity required. But there is an easier way - by leveraging Knowledge Based Access Control (KBAC). Built on a connected graph data model, capturing rich metadata as well as the relationships between entities (people or things), allows you to create flexible and complex authorization policies that can scale indefinitely.
More and more we are seeing clients turn to this type of solution to solve the challenges of how to monetize their data. The right tools with the right strategy can propel your business into a whole new level of value creation.
Want to learn more? Get in touch and we can work with you to identify value creation opportunities.