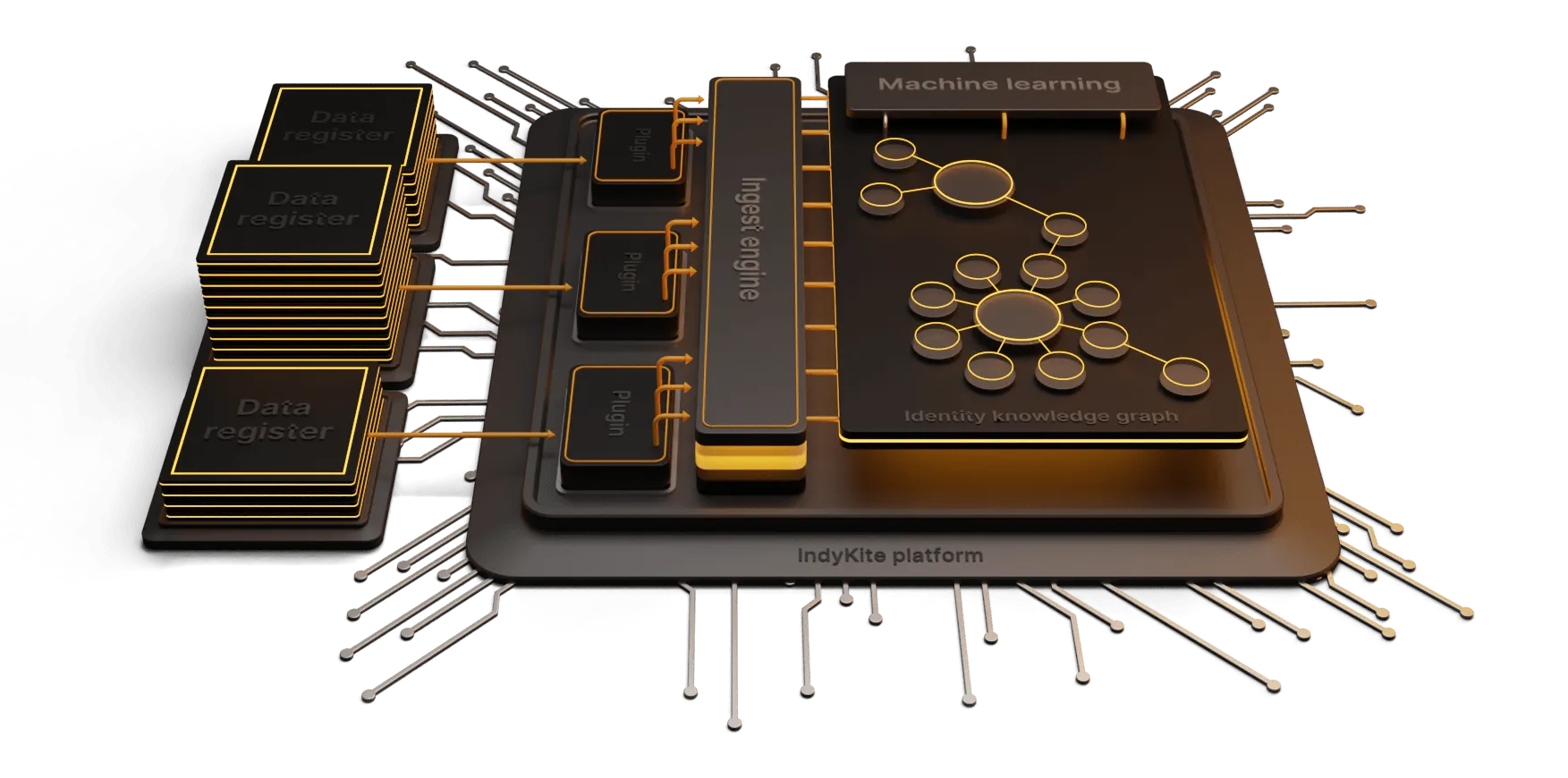
In the last two blogs, we explored what happens after your customers enter the digital door. Your interactions with customers can make or break your business and it seems the stakes are high. They should be -the digital ecosystem can be tricky to navigate and customers are getting vocal! Savvy customers force businesses to provide the best experience possible - this serves as a point of competitive differentiation, a brand loyalty driver and ultimately a revenue generator.
To supercharge your customer experience your business relies on one thing - customer data. How do businesses navigate this tricky territory? We are being faced with business-critical yet seemingly conflicting topics; how to build trust, loyalty and personalized experiences that fuel growth in a world of fading cookies, regulations and privacy-conscious consumers.
It seems we are stuck, or better put, still searching. Data collection and its management is core to this challenge, but current identity methods do not offer acceptable solutions.
Choices are being made on both sides
Many privacy-conscious consumers today opt out of tracking and data sharing upon login and companies are losing the opportunity to better understand their customers leading to billions in lost revenue.
Many businesses today tackle the problem from a pure consent management, compliance and security angle but seem to be forgetting how this data can safely be used to propel your business. Current methods of solving this problem in the identity space are limited and do not capture the challenges of sharing, understanding and connecting identity data. When we are stuck focusing on the compliance side we tend to forget that this data should be used, and it can be, with the right technology!
The time is now to bridge the gap
At IndyKite, we are driven by the core principle that customers should own their data and have simple tools to share data according to their preferences. Data sharing should be dynamic, time and context based, fully transparent and revocable at any time. This principle should not be in conflict with businesses knowing their customers and delivering personalized services. With IndyKite, both realities can exist at the same time.
To solve for the limitations of current solutions, we have introduced Trusted Data Sharing. Trusted Data Sharing gives businesses the tools to interact with their customers with full privacy & transparency, provides industry-compliant data collection and unlocks real-time insights about customers behavior across brands and partner networks. With Trusted Data Sharing, it is possible to to deliver personalized product offerings that are time-based, customer-owned and fully auditable and compliant..
Trusted data sharing delivers growth opportunities, brand trust and customer loyalty
Trusted Data Sharing allows organizations, known as data custodians or data controllers, to collect and use data transparently. Next week we will dive deeper into examples of what this looks like at organizations, but for now, a few more details!
Trusted Data Sharing unlocks three main actions within your organization:
- User-owned sharing: Tooling to empower the user (data owner) to opt-in and opt-out at a granular level.
Building trust and emphasizing transparency with your customers should be one of your top concerns as a business. When you have modern tooling within your applications you can launch data sharing initiatives and provide services in return. Sharing does not need to be a black box - clever campaigns and easy interfaces to share what, why and with whom your customers are sharing data with can drive differentiation.
- User-approved permissions: Services that grant or revoke permission to the use of data at a granular level
When end-users control and fully manage the granting and revoking of permissions to access their data, the organization can use these permissions as a part of an authorization decision. This means full control of the data and its application in your services. Full control helps your business solve complex, granular access control perpetually versus a one-off exercise.
- Compliance and security tracking: Services that allow organizations to track, monitor and audit their programs to ensure compliance
Compliance is necessary and should be a given when working with customer data. Easily and safely understand the flow of customer data to deliver peace of mind to your organization and your customers.
Security and Utility are possible
It is possible to unlock new opportunities for customer experience and new product creation without compromising security with Trusted Data Sharing. Next week we discuss real-world examples and how you can drive more value when you safely operationalize customer data in your organization.